1. You are analyzing the feasibility of your solution. You need additional
information to decide whether the solution is technically possible. Which
additional information do you need?
Case Study
A. A copy of the existing timesheet application.
B. A prototype of the Web application that will be used by Team Leads and
Business Planners.
C. A list of the different models of Windows CE devices that need to be
supported.
D. API information and requirements related to integration with the billing
application.
Answer: D
A: Why would you need a copy of the existing application to see if a new updated
application is feasible?
B: Access to a prototype application will not assist you determine if your
proposed application is feasible.
C: Is not the choice because you don't have to worry about Hand-held devices as
long as they can run Windows CE.
Accounting Manager: We want the new solution to include a utility that
automatically creates invoices in our billing application... the billing
software package is fully programmable. He can provide you with API
documentation...
You would need to ensure that these API will let you satisfy the Accounting
Manager’s. If the API’s cannot satisfy the requirements then that will greatly
affect the feasibility of the project.
2. You are writing the operational requirements document for your solution.
Which should you include?
Case Study
A. The application must encrypt all time entry data on client computers and
in the database, and data must be encrypted when transmitted over the internet.
B. The IT staff will be responsible for fixing bugs in the code.
C. The IT staff must be alerted to application problems.
D. The application can have no single point of failure.
Answer: C
A: There is a requirement that the app is secure – but encrypting the content of
the database goes way over the top. The requirement just specifies secure and
that users are authenticated.
B: The IT staff are not programmers, so wouldn’t be able to fix bugs.
D: There is no requirement for this.
The new application must include tools that alert us to all failures and help us
resolve failures.
3.
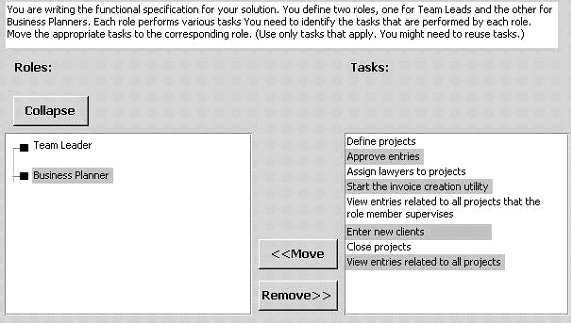
Case Study
A. Team Lead - View entries related to all projects that the role member supervises, Approve entries
B. Business Planner - Views entries related to all projects, Enters new clients, Defines Projects, Closes Projects, Assigns lawyers to projects
C. Team Lead - Views entries related to all projects, Starts the invoice creation utility
D. Business Planner - Approves entries, Views entries related to all projects that the role member supervises, Enters new clients
Answer: A, B
Left out "Start the invoice creation utility" because it is performed by the
Accounting Manager.
4. You are writing the technical specification for your solution. Your new
timesheet application must be able to access timesheet entry data. You need to
specify the technology that will be used for accessing this data. Your solution
must require the minimum development effort. Which technology should you use?
Case Study
A.a SQLConnection class
B.a .NET Remoting object that uses TCP channel and binary formatting
C.an XML Web service proxy class
D.an interop assembly
Answer: C
Lawyer, Corporate Law Division : When we work at home, we want to be able to use
the application over the internet. When we do so, the application should update
the data immediately.
To get the data to update immediately… a data layer webservice will have to be
called from the winform app ! This can Be accomplished by using an XML Web
service proxy class to make the call.
A: SQLConnection is a class, that is part of ADO.NET Technology. This class on
its own is not enough for data access.
B: not a good idea since we have firewall and port restrictions.
D: This makes no sense. An interop assemble as a way to access data. They are
just giving it a tug.
5. You are writing the technical specification for your solution. You need to
select a technology for the new timesheet application. Which technology should
you use?
Case Study
A. an XML Web service
B. a Web application
C. a console application
D. a Windows Forms application
Answer: D
Because they want a taskbar type application that sits on the side of the screen
and then pops out... plus a GUI frontend for sorting and other jazz, this lets
me believe that they want a Windows Forms Application. To be able to update
their data from home, they will use SOAP (XML over HTTP) via an XML Web service
to update the data (See question 4) !
A: An XML Web Service doesn’t have the type of user interface required to build
the application.
B: The Lawyers want a SWISH looking app with lots of cool functionality. I don't
think you'll be able to get this type of functionality out of a Web Application
!
C: Its obvious
6. You are creating a high level class diagram for your solution. You need to
add one or more business entities to the diagram. Which entity or entities
should you add? (Choose all that apply)
Case Study
A. Task time
B. Pop-up window
C. Project
D. Lawyer
E. Client
F. Task description
G. Time entry
Answer: C, D, E, G
A: Task time is part of a time entry.
B: A popup window is not a business object.
F: Task Description is also part of the time entry.
7. Class Diagram Definition
You are writing a conceptual diagram of the modules that must be developed
for your solution. Which module or modules should be included? (Choose all that
apply)
Case Study
A. a Web application for Team Leads and Business Planners
B. a timesheet entry database
C. a billing database
D. a notification engine that sends timesheet entry reminders
E. a timesheet entry application
F. a Windows CE application
G. a utility that uploads information to the billing application
Answer: A, B, E, F, G
D: This is not a requirement
B: [NOT SURE ABOUT THIS] You don't worry about data storage in Conceptual design
by separating timesheet data from billing data. I think a database IS a module
and therefore B is needed !
Questions ask for "modules" that "must" be developed. E, G is a must have.
Conceptual design includes physical environment where application will reside.
so A, F are OK too. Reminder is not a "must" have feature.
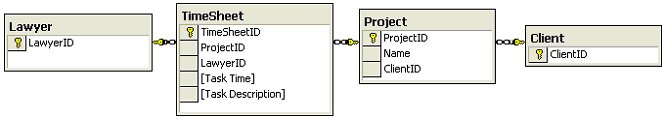
8. A database architect on your team prepares a logical data model. The model
includes entries that correspond to clients, projects and timesheet entries. You
are reviewing the model. Which entity relationship or relationships should be
included? (Choose all that apply)
Case Study
A. a Project entity is the parent of a TimesheetEntry entity
B. a Client entity is the child of a TimesheetEntry entity
C. a many-to-many relationship exists between a Client entity and a Project entity
D. a many-to-many relationship exists between a Project entity and a TimesheetEntry entity
E. a Client entity is the parent of a Project entity
F. a Client entity is the parent of a TimesheetEntry entity
Answer: A, E
B: Why would a client (of which there would be only a few) be a child item of a
timesheet entry (of which there would be heaps, and many added every day).
C: A client can have many projects, but a project can have only one client.
D: A project will have many timesheet entries, but a timesheet entry will have
only one project
F: Timesheets belong to projects, not clients.
Each timesheet entry is billable to a project. A given client might have several
ongoing projects. Each timesheet entry includes a time, a lawyer and a task
description.
9. The Web application used by Team Leads and Business Planners requires an
authentication mechanism. Which pair of authentication technologies should you
recommend?
Case Study
A. IIS Anonymous authentication with ASP.NET Passport authentication
B. IIS Anonymous authentication with ASP.NET Forms authentication
C. IIS Basic authentication with SSL and ASP.NET Windows authentication
D. IIS Integrated Windows authentication with ASP.NET Windows authentication
E. IIS Basic authentication with SSL and ASP.NET Forms authentication
Answer: C
A, B: The IT Manager: Any Web application or application endpoint exposed to the
Internet must require authentication. I am assuming that the Anonymous
authentication fails this requirement. One reason I think that if the Anonymous
authentication was okay provided that the application authenticated users then
either A or B would be okay.
D: Firewall restricts incoming traffic to HTTP connections on TCP ports 80
(HTTP) and 443 (HTTPS). The IT staff will not open additional ports.
Because of the firewall restrictions, IIS Integrated Windows authentication
cannot be used because it requires additional ports to be open. Kerberos uses
port 88. There are other ports as well like 464 (kpasswd) and 543 (klogin).
E. This would work, but is less than ideal. Using ASP.Net forms authentication
you will need to somehow maintain a list or database of valid users, and provide
some way for them to change their passwords. Using Windows authentication you
don’t have to worry about that
Each employee has a Windows 2000 domain user account (Existing IT Environment),
from this, ASP.NET Passport & Forms are out so that leaves (C) & (D).
C works because the User Name and Password as passed in as strings in clear text
which can work through port 80 & 443. Because of this, Microsoft recommends
using SSL with IIS Basic authentication.
10. You are designing a strategy to migrate data from the existing timesheet
application to the new application. Which tool or technology should you use?
Case Study
A. XML Schema Definition tool (xsd.exe)
B. COM interoperability
C. Microsoft SQL Server Data Transformation Services (DTS)
D. Microsoft SQL Server replication
Answer: C
Without a doubt... this is THE way to go !
11. The invoice creation process must be dynamically monitored to track the
following information:
• Average number of seconds to create an invoice
• Number of invoices created per second
• Total number of successfully created invoices
• Total number of failed attempts to create an invoice
Monitoring should occur with a minimum of development effort. What should you
do?
Case Study
A. Write statistics to the database and use SQL Query Analyzer to dynamically monitor the statistics
B. Create a remotable Microsoft .NET class to contain statistics. Configure the class as singleton class. Write a utility that retrieves
statistical information from this class
C. Write statistics to the application event log
D. Use custom performance counters
Answer: D
A: Writing the statistics to the database would work, but is more effort. But
SQL Query Analyzer will not dynamically monitor statistics.
B: Way too much effort.
C: This would work, but viewing and analyzing the stats would be a pain. Using
performance monitor is much easier.
Using custom performance counters will let you collect, monitor and analyze
performance statistics through Windows performance monitor.
12. The Web application used by Business Planners generates many types of
reports. One type displays billing information over specified timeframes. The
other selects a lawyer and a timeframe and the report displays the average
number of minutes billed by that lawyer per day and the average number of
minutes billed to each client per day over that timeframe. You must ensure that
this report is generated with a minimum network traffic. What should you do?
Case Study
A. Use Microsoft SQL Server indexes to optimize the data calculations
B. Implement the calculations in a business layer class
C. Implement the calculations in a data layer class
D. Use Microsoft SQL Server stored procedures for the data calculations
Answer: D
Only doing the calculations on the server in a Stored Procedure will minimize
the network traffic.
13. You are validating the physical design of a data a data layer class that
will return a set of time entries from the timesheet database. This class will
be used by the Web application for Team Leads and Business Planners and,
indirectly, by the new timesheet application. The class must use connection
pooling, and it must be as secure and as flexible as possible. You need to
specify a Microsoft SQL Server authentication strategy that meets these
requirements. Which strategy should you use?
Case Study
A. The data class uses SQL Server authentication with an application specific SQL Server account. The account name and password are embedded in a
connection string
B. The data class uses Windows authentication when connecting to the database and impersonates a specific account created for operations on the
database
C. The data class uses Windows authentication when connecting to the database and impersonates the application user
D. The data class uses SQL Server authentication with the SQL Server sa account
Answer: B
A: is incorrect because it prevents storing database usernames and passwords in clear text, and allows for more thorougly integrated passwords.
C: will not allow Connection Pooling because of impersonation.
D: is NOT secure... applications should never use the sa account.
You have to use application role not Windows ID.
14. In your first code review, you detect several violations of your policies.
The following examples are typical violations:
• Data controls are used in presentation layer components
• Windows UI elements are added to Web UI projects
• Shareware user controls are used
You must establish and enforce standards to prevent these kinds of violations.
You want to enforce the standards with a minimum of administrative effort. What
should you do?
Case Study
A. Base projects on an appropriate Microsoft Visual Studio .NET Enterprise Template
B. Conduct more frequent code reviews
C. Use Active Template Library projects
D. Write a utility that uses Microsoft .NET reflection to examine compiled code for inappropriate types
Answer: A
B: More frequent code reviews would be time consuming and not required.
C: Active Template Library projects are for C++.
D: Get real! Why would you want to examine compiled code for inappropriate
types? That is just silly.
Enterprise Templates are provided to simplify application creation and to
provide policy that warns users when they violate recommended guidelines. Source
15. Your team builds a daily release of the timesheet application for testing by
the quality assurance (QA) team. You find that the volume of bugs is threatening
your project schedule. The following example is a typical bug: One method should
return a dataset that is based on a date range given as input parameters.
However, when the method queries the database, it erroneously interchanges the
beginning date and the end date. An empty dataset is always returned. You need
to minimize these kinds of bugs using a minimum of development effort and QA
effort. What should you do?
Case Study
A. Require more frequent builds
B. Require the QA team to perform more integration testing
C. Require engineers to perform complete integration testing before submitting code
D. Require engineers to perform adequate unit tests before submitting code
Answer: D
A: This not going to FIX problem.
B: QA team not going to fix your code problem.
C: My understanding of integration testing is that addresses how different
system components work together. If the example bug was a system integration
issue the method would work fine by itself, but there would be a problem in how
another system component called it. For example, the calling procedure correctly
gave two date parameters to the method, but it mixed up the start date and end
date.
In that example the method is capable of providing a correct answer, but doesn't
in that particular case because it is not called correctly - so that is an
integration issue.
The reason I go for unit test is the example bug provided in the question. The
bug in the method call will return an empty dataset 100% of the time. Sure that
will cause problems in system integration, but it would also cause problems if
anything in the same module called that method.
In the example in the question the method is incapable of providing a correct
answer under any circumstances, so to me that is a unit test issue.
16. Which business constraint poses the greatest potential risk to completing your project for Blue Yonder Airlines?
Case Study
A. The scheduling vendor will begin providing access by XML Web service in three months
B. The application must be completed within a five-month development period before it is tested
C. The current IT staff must support the solution in the future
D. All testing scenarios and all necessary rework must be completed during the one-month testing period
Answer: A
B: Since there is enough funding it shouldn’t be a problem.
C: The question is asking for risks to COMPLETING THE PROJECT. This does not have any impact.
D: This is all a matter of resources.
Business Manager says that the vendor only meets its deadlines for delivering updates only 50 percent of the time. This will have the greatest impact.
17. You are looking the operational requirements for the new reservation application. Which requirement should you include?
Case Study
A. Availability
B. Deployability
C. Maintainability
D. Extensibility
E. Localization
Answer: A
C, D: Are needed, but this is not a "Choose all that apply" question.
E: No mention of Localization in the case study.
The Chief Executive Officer, who is a Business Stakeholder, wants to allow customers to make reservations at any time, on any day of the week.
18. You are preparing the functional specification for the new reservation application. Which two functionalities should you specify? (Each correct answer presents part of the solution. Choose two)
Case Study
A. Monitoring application performance
B. Availability of application for mobile phones and personal digital assistants
C. Integration with Active Directory
D. Secure storage of customer profile information
E. Localization
Answer: A, D
B: There was no request for that.
C: Has nothing to do with this.
E: Shouldn’t be important, I found no request for multiple languages and I doubt that the reservation agents were multilingual.
Monitoring and confidentiality were direct requests.
19. You need to select a strategy that will provide detailed usage information for the new reservation application. Information must be provided with a minimum development effort. What should you do?
Case Study
A. Use Microsoft .NET performance counters in the application.
B. Create a Microsoft Management Console (MMC) snap-in for the application.
C. Add Windows Management instrumentation to the application.
D. Use the application’s configuration file to enable and disable logging.
Answer: A
20. You are completing the technical specification for the new reservation application. Which technique should you recommend for state management?
Case Study
A. Server-side database
B. Client-side cookies
C. Application cache
D. ASP.NET ViewState
Answer: A
B: They may not be allowed on the client machine’s browser.
C: Makes no sense to me to put it there.
D: This will be gone when the customer closes the session.
Retrieve a saved itinerary and initiate booking for the flights saved in the itinerary. Sure, we can say B, but if client will change PC?
21. During the conceptual design phase, you create the Customer fact as shown in the Customer Fact Diagram. Then you try to validate the population data shown in the Population Data Diagram. However, validation fails. What should you do?
Customer Fact Diagram
Population Data Diagram
Case Study
A. Add a unique constraint to the Name field
B. Change the Customer reference mode to Name plus City
C. Change the Customer reference mode to CustomerID
D. Add a mandatory role constraint to the CustomerID field
Answer: C
22. Your development team proposes four different conceptual designs for the new reservation application. You need to present one of these designs to the board of directors of Blue Yonder Airlines. Which design should you present?
Case Study
A.

B.
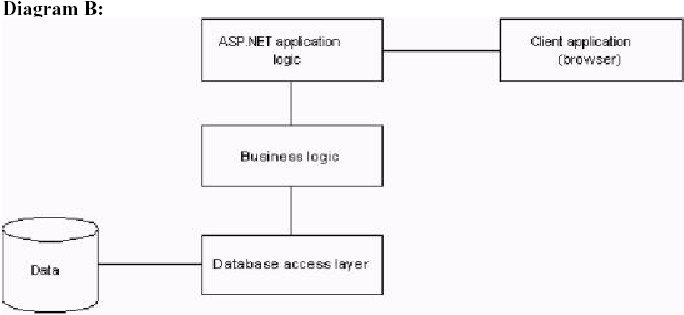
C.
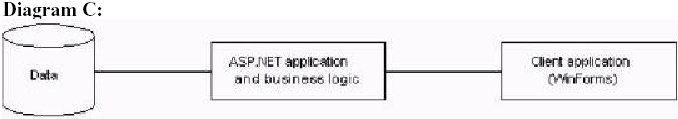
D.
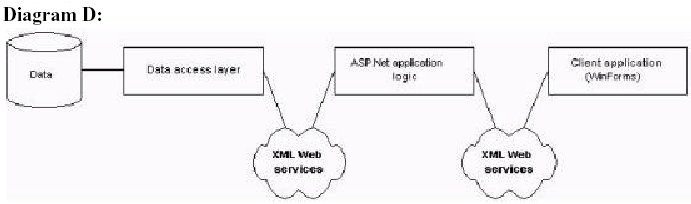
Answer: B
D is not possible because 2 web services and a client winForms application!
23. You are creating constraints for tables named Flight and Airport. You must ensure data integrity. Which action or actions should you take? (Choose all that apply)
Case Study
A. Create a primary key constraint on the AirportCode column and the CityOfOrigin column in the Airport table
B. Create a primary key constraint on the FlightNumber column in the Flight table
C. Create a cascading delete constraint on the AirportCode column in the Airport Table
D. Create a foreign key constraint on the ArriveAirportCode column in the Flight table to reference the AirportCode column in the Airport table
E. Create a primary key constraint on the FlightNumber column, the FlightDate column and the DepartAirportCode column in the Flight table
F. Create a foreign key constraint on the DepartAirportCode column in the Flight table to reference the AirportCode column in the Airport table
G. Create a primary key constraint on the AirportCode column in the Airport table
H. Create a foreign key constraint on the AirportCode column in the Airport table to reference the DepartAirportCode column in the Flight table
Answer: D, E, F, G
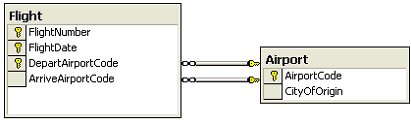
A: Shouldn’t be a primary key cause flight numbers stay identically.
One Airport has many Flights.
CityOfOrigin is not necessary to uniquely identify records within the Airport Table.
AirportCode is unique enough.
FlightDate DEFINITELY has to be part of the composite key within the Flight Table.
Having a cascade delete is a nice-to-have option on the database. It isn’t essential.
If you wish to delete an airport, you have 2 options :
o Delete all the related Flight records (programmatically) then delete the Airport record.
o Delete the Airport code and let the database delete all related flight children records.
The question is… where do you want the control ? On the database or via an application. Enabling cascading delete is a nice to have luxury on the database … but it IS NOT essential as the 2 foreign keys on the AirportCode are enough to ensure that data integrity is maintained.
24. You are creating the logical design for the new reservation application. Which entity or entities should you include? (Choose all that apply)
Case Study
A. Airport
B. Customer
C. Gate
D. Flight
E. City
Answer: A, B, D
C, E: These would be attributes.
A, B, D: Are definitely needed. City should be entity or an attribute. It would be needed if we wanted to populate a select list or if we wanted in impose a Foreign Key Constraint on city in the other tables.
I don’t think City is necessary as the Airport will exist within a city… therefore the Airport implies the city. (See database diagram in previous question).
And… think of any online flight booking website… do you select the airport and also the city (e.g. LHW – London Heathrow)… ? No ! You select only the airport. The airport already exists within a city… hence… I don’t think City is really that necessary !
25. You are creating the logical design for a use case named "Customer updates Customer Profile". Which object or objects should you include in the design? (Choose all that apply)
Case Study
A. Customer object
B. Flight object
C. Logging object
D. Data access object
E. Airline object
Answer: A, C, D
B, E: these are not related to the use case named "Customer updates customer profiles".
A, D: Are definitely needed for the use case in question.
C: Business Manager does want logging of detailed usage information for analysis.
26. You need to implement online interactive user assistance for the new reservation application. What should you do?
Case Study
A. Create a manual that can be downloaded from the Web site
B. Create a compiled help module and use context-sensitive help for all screen elements
C. Implement ToolTips to provide information about all screen elements
D. Use the ALT attribute to provide a short textual description for all images and audio files
Answer: C
A: This is considered offline.
B: I think this is more for Windows Applications instead of Web Applications.
D: This is normally used for people with disabilities.
Providing online user assistance
Even the best user interface design and input validation procedures cannot ensure that your users will be able to know what to do and when to do it. To avoid personally training and supporting every user through their individual learning curves, you need to make some form of online user assistance in a format they are able, willing, and ready to call up. The most common ways to do this are through the use of status bars, tooltips, and application help files.
27. You must ensure that the new reservation application can be monitored while is running. Which approach should you use?
Case Study
A. Windows Management Instrumentation Job Object provider
B. PerformanceCounter objects
C. TraceSwitch objects
D. Diagnostic tools
Answer: B (See Q4)
C: TraceSwitch Class - Provides a multilevel switch to control tracing and debug output without recompiling your code.
We talking about monitoring, not about tracing and debugging.
28. You are writing the primary scenario of a use case named "Customer retrieves a Saved Itinerary". Which action or actions should be included? (Choose all that apply)
Case Study
A. Application informs customers that no itineraries exist.
B. Application informs customers that a saved flight is no longer available.
C. Customer asks for saved itineraries.
D. Application offers alternate flights.
E. Application queries the database for saved itineraries.
F. Application displays retrieved itineraries.
Answer: C, E, F
The question is asking for the Primary Scenario.
29. You need to identify the kinds of Testing that should be performed on your software. You also need to specify the order in which testing should occur. Most the appropriate actions from the Possible Actions pane to the Ordered Actions pane and arrange them in the appropriate order. (Use only actions that apply)
Case Study
Possible Actions
Regression Testing
Single stepping through code
System testing
Unit testing
Network bandwidth testing
Database disk I/O testing
Peer code review
Integration Testing
A. Unit testing, Integration testing, Regression testing, System testing
B. Single stepping through code, Unit testing, Peer code review, Integration testing
C. Unit testing, Regression testing, System testing, Integration testing
Answer: A
So, question is: Should we assume that Network and Disk I/O testing is parts of load testing or not? I think - No.
Here are extracts on Testing Web Applications which is in Chapter 10 of the Microsoft Press book MCAD/MCSD Self Paced Training Kit - Developing Web Applications with Microsoft Visual Basic .NET and Microsoft Visual C# .NET.
30. You are establishing a policy to measure the effectiveness of your deployment process. You decide to track one or more phases of development to identify defects. Which phase or phases should you track? (Choose all that apply)
Case Study
A. Design and analysis
B. Development
C. Stabilization
D. Requirements
Answer: B, C
31. Which solution concept should you recommend for bill presentment?
Case Study
A. Banks communicate an XML Web service to access customer billing data.
B. Each bank has an XML Web service for submitting bill presentment data.
C. Banks provide customer billing data to an XML Web service.
D. Each bank has an XML Web service for receiving bill presentment data.
Answer: A
B,D: It is City Power and Light who needs to provide the web service, not the banks.
C: The XML Web Service provides banks with customer billing data.
32. You are creating the functional specification for your solution. Which bill presentment requirement should you include?
Case Study
A. Communicate with a secure programmatic interface for bulk loading of customer billing data when the data changes.
B. Provide a secure programmatic interface for bulk loading of customer billing data.
C. Provide a secure XML Web service for presenting individual customer billing data.
D. Communicate with a secure XML Web service for loading individual customer billing data.
Answer: C
IT Manager: If we expose any programmatic interfaces that are externally accessible, they must be available only to authenticated users. These interfaces must also use secure transport. Chief Executive Officer: Security is also very important. Unauthorized users must not be able to view billing data or bill presentment data that relates to our customers.
A, B, D No requirement in case study.
33. You are creating the conceptual design for your solution. Which entity or entities should you include? (Choose all that apply.)
Case Study
A. Meter read
B. Customer
C. Billing schedule
D. Bank
E. Credit card
Answer: B, D, E
B and D are obvious.
E: Because the Chief Financial Officer wants to allow each customer to pay bills by using one or more credit cards. Otherwise, this would have been an attribute of Customer instead of an entity.
34. You are validating the logical data model for your solution. Which attribute or attributes should be included in the Customer entity? (Choose all that apply.)
Case Study
A. Password
B. Customer Identifier
C. Bank Identifier
D. Bill Identifier
E. Credit Card Number
Answer: A, B
C, D: These should not be included in the Customer entity.
E: Chief Financial Officer wants to allow each customer to pay bills by using one or more credit cards. So after normalization, this should not be in the Customer entity.
A: IT Manager- All customers have unique account numbers. Customers will need to create passwords and enter them when they use the new customer Web site to pay bills
B: Primary Key for Customer entity.
35. You need to create the physical design for the authentication mechanism in the bill presentment module.. What should you do?
Case Study
A. Pass authorization credentials in SOAP headers.
B. Include a WindowsPrincipal parameter in every Web method.
C. Create a single authentication service that has authentication parameters.
D. Include a Generic-Principal parameter in every Web method.
Answer: A
B: Not using IIS Windows authentication.
C: ?
D: Not using Windows accounts.
Client application communicates with an XML Web service by sending and receiving SOAP messages over Hypertext Transfer Protocol (HTTP).
Windows Principal object
The System.Security.Principal namespace within the .NET Framework Class Library (BCL) provides a WindowsPrincipal object to represent the security context under which the code is running. This object is created for you automatically when you use Windows authentication in IIS. It allows you to check the Windows group membership of a Windows user and restrict access accordingly.
Generic Principal object
A Generic Principal object can be created based on your own custom roles. You will use this when you have your own user/role database. The Principal object is populated in the OnAuthenticate event. You may have a custom table mapped to Windows accounts that you map in this event. In any case, you can create a custom Principal object for that particular user.
Authentication in ASP.NET: .NET Security Guidance
36. Simple logical errors often occur in your daily builds. You need to recommend improvements in the build process. Which action or actions should you recommend? (Choose all that apply.)
Case Study
A. Developers must create and perform unit tests.
B. Developers must instrument code before checking it in.
C. All errors must be logged in an error-tracking application.
D. Developers must write comment for classes, methods, and properties.
E. Quality assurance testing must be performed on all assemblies.
Answer: A, B, E
37. Which new business process or processes should be supported by the new solution? (Choose all that apply)
Case Study
A. Bar code readers are supported.
B. Brokers can order transportation services.
C. Use of space on vehicles can be tracked.
D. Vehicle scheduling capability is provided.
E. Customers can track parcels.
F. Brokers can track shipments.
Answer: B, C, F
B: The new service will enable the independent brokers to use the company’s vehicles to send large shipments between cities.
C: The existing vehicle-scheduling application does not track the amount of space that is being used on each vehicle at a given time. However, the new solution should enable us to track this information.
F: These brokers must be able to use the Internet to schedule their own shipments.
A: ...bar code is scanned at various checkpoints in the shipment process.
D: Vehicles are scheduled one month in advance...
E: Customers use the Internet to track the shipping status of their parcels.
38. You are validating your conceptual design in terms of scalability. Which requirement will probably have the greatest impact on scalability?
Case Study
A. Reporting use of space in vehicles.
B. Using the interface to bar code readers.
C. Scheduling additional vehicles.
D. Handling additional broker shipments.
Answer: D
The new service will enable the independent brokers to use the company’s vehicles to send large shipments between cities. Each shipment will consist of a large number of parcels. The company’s existing business applications must be enhanced to support the new service. Source
39. You need to ensure that transportation brokers are authenticated when they access the broker Web site. Which action or actions should you take? (Choose all that apply)
Case Study
A. Secure the exchange of user names and passwords between the client computer and the server.
B. Provide a facility to view passwords.
C. Create a distribution list of authenticated users.
D. Provide a facility for online registration.
E. Enable e-mail access for transportation brokers.
F. Provide secure storage of user names and passwords.
Answer: A, D, F
...ensure that transportation brokers are authenticated... So, we need facility for the registration + ability to send encrypted credentials + storage for this info - so we can compare logon data with stored ones.
40. You need to enable brokers to track their own shipment. To meet this requirement, you need to consider various specifications. Which four specifications should you consider? (Each correct answer presents part of the solution)
Case Study
A. Provide a Web-accessible form to authenticate brokers against a table of registered users.
B. Provide a Web-accessible form to enable brokers to request vehicle routes for their shipments.
C. Provide a Web-accessible form to query the database for broker shipments.
D. Provide a Web-accessible form to generate waybill numbers.
E. Identify a parcel in the database as part of a broker shipment.
F. Relate a parcel to a specific broker.
G. Track the weight of a parcel in the database.
Answer: A, C, E, F
A: Form to authenticate brokers - So brokers can log in.
C: Form to query the database for broker shipments - Brokers need to know about their shipments
D: Form to generate waybill numbers - Broker requests service and is issued a waybill number. (NOT SURE ABOUT THIS)
E: Identify a parcel in the database as part of a broker shipment - Brokers can do this track the parcel as it is shipped.
B: Form to enable brokers to request vehicle routes for their shipments - Brokers request the service (if it is available) not the routes.
F: Relate a parcel to a specific broker - Brokers are not allowed to know about other brokers shipments, can only relate their parcels to themselves (not to brokers in general). (NOT SURE ABOUT THIS)
G: Track the weight of a parcel in the database - This not a requirement.
41. When the new solution is in place, parcel information and parcel history information must be stored. You need to estimate the amount of data that will be generated by the new solution during its first year of use. What is the approximate amount?
Case Study
A. 824MB
B. 5GB
C. 8GB
D. 50GB
Answer: C
Size = 100,000 parcels every week * 52 weeks * 20% increase * 1 KB / 1,048,576 KB = 5.95 GB
Trick is - catch everybody who missed 20%.
42. Which data item or items should you add to the existing applications? (Choose all that apply)
Case Study
A. Waybill information.
B. Broker identification information.
C. Parcel routing information.
D. Depot information.
E. Parcel dimensions.
F. Information about use of space on vehicles.
Answer: B, E, F
B, E is obvious.
F: The existing vehicle-scheduling application does not track the amount of space that is being used on each vehicle at a given time. However, the new solution should enable us to track this information.
43. You need to decide whether your conceptual design represents a complete solution. Which four design artefacts are relevant to your decision? (Each correct answer presents part of the solution. Choose four)
Case Study
A. Component prototypes for tracking shipments.
B. Use cases for authenticating brokers.
C. Functional requirements for tracking shipments.
D. Component prototypes for authenticating brokers.
E. Functional requirements authenticating brokers.
F. Unit test for authenticating brokers.
G. Use cases for tracking shipments.
H. Unit test cases for tracking shipments.
Answer: B, C, E, G
Conceptual views are the most abstract and tend to be described in terms that are most familiar to the (non-IT professional) users of the system. The conceptual view is used to define the functional requirements and the business users' view of the application to generate a business model.
The conceptual view is used to define the business requirements and the business users' view of the application to generate a business model. Conceptual modelling techniques, such as use case analysis, activity diagrams, process design, and business entity modelling, help to build a description of the key business processes and the data they use, in way that emphasizes business objectives and requirements, and is free of implementation technology. Source
Definition of Conceptual Design from MOC 2710A: View the problem from the perspective of the user and business requirements and define the problem and solution in terms of usage scenarios.
Definition of Artefact from MOC 2710A: An item that is physically available in the business environment and that describes an element or core business process.
44. You are creating the logical data model for associating vehicles with routes. Use entities and relationships to create a diagram that illustrates your solution. (Use only entities and relationships that apply. You might need to reuse relationships.)
Case Study
A.

B.

C.

D.

Answer: A
The Route Instance table associates a specific vehicle with a defined route. So, Route Instance - simple associative table.
45. Your development team creates four different logical designs for the solution. Which design should you use?
Case Study
A.

B.

C.

D.

Answer: C
A: There is no interface between the vehicle scheduling application and the parcel tracking application
B: The scheduling and tracking of broker shipments is part of the parcel tracking application, not the vehicle-scheduling application.
D: There are definitely 2 separate databases.
46. You are creating the design for shipment scheduling functionality. You need to identify which modules are associated with this functionality and how they will interact. Use available modules and protocols to create a diagram that illustrates your solution. (Use only modules and protocols that apply)
Case Study

A. Web Browser -> HTML over HTTP -> ASP Page for Shipment Scheduling -> ADO.NET -> Method Invocation -> Schedule Component
B. Schedule Component -> Method Invocation -> ASP Page for Shipment Scheduling -> XML over HTTP -> Web Browser
C. Web Browser -> HTML over HTTP -> ASP Page for Shipment Scheduling -> XML over HTTP -> Method Invocation -> Schedule Component
D. Web Browser -> HTML over HTTP -> ASP Page for Shipment Scheduling -> Method Invocation -> Schedule Component
Answer: D
47. The parcel-tracking application uses a table named Parcel. You need to modify the schema for this table to support the requirements of your solution. Create a diagram that illustrates your modifications. Move the appropriate data elements to the appropriate location in the schema. (Use only data elements that apply. You might need to reuse data elements.)
Case Study

A. Primary key: Leave alone
Attributes: Height, Width, Length
Foreign Keys: Customer Type, Broker ID
B. Primary Key: BrokerID
Attributes: Height, Width, Length
Foreign Key: Customer Type
C. Primary Key: Leave alone
Attributes: Height, Width, Length, Customer Type
Foreign Key: BrokerID
D. Primary Key: Customer Type
Attributes: Height, Width, Length
Foreign Key: Customer Type
Answer: A
The Parcel table already exists within the database. We are simply modifying it.
So… no need to add to the Primary Key as this has already been setup previously.
Height, Width and Length are attributes (this is easy).
Broker Identifier is a new field that identifies the Broker from the Broker Table.
This Broker table will be new…. So we need a foreign key in the Parcel table to reference the Broker Table. Before… this application was only used for trucks.
Now parcels can be of 2 types… :
- A Package belonging to Consolidated Messengers
- A Package belonging to a Broker.
So… I see a new table being created: a separate Customer Type table to identify if a package belongs to a broker or to the company. Hence… a 2nd foreign key : Customer Type.

48. You are validating the physical design for your solution. Which element or elements should be included in the design? (Choose all that apply)
Case Study
A. Algorithms for scheduling vehicles.
B. Scalability to meet increased usage.
C. Authentication of transportation brokers.
D. Interface to the bar code readers.
E. Online registration facility for transportation brokers.
Answer: B, C, E
Physical views are the least abstract and illustrate the specific implementation components and their relationships.
Also Chap 6 "Creating the Physical Design" page 234 in MS .Net Sol. Arch. for exam 70-300 Scalability is a design consideration
49. Which performance standard should you use for your solution?
Case Study
A. Screen response time of two seconds or less.
B. Vehicle usage of at least 80 percent of total capacity.
C. Database size of less than one terabyte.
D. CPU utilization of less than 50 percent in the database server.
Answer: A
B: Vehicle usage as far as I understand not related to performance standard for your solution.
C: There is no such requirement.
D: It can be right answer, but according to Depot Manager interview:
Response time for the bar code readers must be fast enough to handle the new shipping volume, without any errors. Response time for the vehicle-scheduling application must also be fast. Delays in updates can delay a shipment or reduce the amount of space used on a vehicle.
And also:

Response time
Response time is a very important requirement. The industry standard for response time is a maximum of three seconds. (Source)
50. Before you release the solution, you need to develop a process to validate and enforce an appropriate level of quality. Which three statistics should you use? (Each correct answer presents part of the solution)
Case Study
A. Percentage of requirements tested
B. Number of defects per component
C. Number of defects detected to date
D. Number of defects corrected to date
E. Number of defects by developer
F. Percentage of successful builds
G. Number of defects per thousand lines of source code
Answer: A, C, D
C,D: should go together. These two are usually used to monitor Bug Convergence (an interim milestone of the Stabilizing Phase of the MSF process model).
E: We do not measuring developer's professional level.
51. Which module or modules should you include in your solution concept for Fabrikam, Inc? (Choose all that apply)
Case Study
A. Data store.
B. Interface to mainframe computer
C. Web site for customers
D. Feature set for ordering raw materials
E. Web site for salespeople
Answer: A, B, C, D, E
Guys, I don't understand - why everybody think that the solution will include a WEB SITE for SALESPERSON? Is there any requirements about SITE?
The solution will include a new customer Web site.
Our salespeople need access to customer information and order history when they are in the office and when they travel in the field.
We going to include role-based identification. (Bronze, Silver or Gold categories). Just add one more - Salesperson - and add reporting and some additional functionality for this role...
A: We talking about modules. And some of you thinking that Data store is not a module. Database (SQL, Oracle,...) is not a module. Data store IMHO might be a module.
B: is needed because the IT Manager does not want to add or modify the mainframe applications.
C: The solution will include a new customer Web site.
D: is need because the Manufacturing Manager wants this.
52. You are writing a document that identifies potential project risks. Which business constraint poses the greatest potential risk?
Case Study
A. The solution must be hosted by Fabrikam, Inc
B. Testing and deployment of the customer Web site must be complete in six months
C. The shipping partner will deploy the XML Web service in four months
D. All customers will try to place orders at the end of the month
Answer: D
A: Not an issue. I don't see why this is a risk.
B: While this may be considered a Business Constraint, I wouldn't specifically consider this the greatest potential risk.
C: This would be my 2nd choice although this is not a real issue if the shipping partner has a good track record. There is no mention of a poor track record like in the A.Datum Corporation Case Study.
This is another tricky question. The question states "Business Constraint".
IT Manager (and project owner) highest priority is to make the customers happy. CFO wants the scope of the project to maximize benefit to customers.
If all customers attempt to place orders at the end of the month, the system might be overloaded. This affects the "happiness" of the customer. However, this is occurs once a month which may not be enough to justify scaling, and the Chief Financial Officer has mentioned limited amount of money to spend.
Because the Mainframe can only handle 2 concurrent TCP/IP connections at the same time… imagine 5000 customers (and more) trying to purchase kites on the last day of the month at about lunch time ? (for example). The response to the website will be SOO bad that they’ll never want to come back to the website !! The 2 concurrent TCP/IP connections to the mainframe is a potential show stopper !!
53. You are writing a list of integration requirements for your solution. Which requirement or requirements should you include? (Choose all that apply)
Case Study
A. Order data must be read from the accounting application
B. Shipment tracking must be read from an XML Web service
C. Customers must be redirected to another We site to track shipments
D. Customers must be able to place orders by using an XML Web service
E. Order data must be written to the accounting application
F. Order data must be e-mailed to the salespeople
Answer: A, B, E
C: IT Manager has specifically stated that customers should NOT be redirected to another site.
D: The customer should be able to place orders over the internet... but using a Web Application... not an XML Web Service.
F: Order data must be e-mailed to the customer... not the salespeople.
A: The Accounting Application is going to stay. So Order DATA should remain as well. And also, since we writting data to accounting application, we going to read from an accounting application.
B: Shipping partner is delivering this in four months.
E: Same reason for A.
54. You are writing the functional specification for your solution. You must include the customer pricing requirements. Which requirement or requirements should you include? (Choose all that apply)
Case Study
A. Pricing data must be encrypted
B. Each user must be uniquely identified
C. Content must be personalized by user
D. Order data must be read from the accounting application
Answer: B, C
A: Since we only let the customer see his data and prices there should be no need to encrypt them.
D: The company uses an accounting application to manage the customer billing process.
It responds to requests slowly and supports a maximum of two concurrent TCP/IP connections.
I want to store category pricing as part of the new solution. I want also the ability to change pricing every quarter.
I don't understand how order data can be related to customer pricing requirements.
B: It's obvious - identified by role.
C: Comes from requirements.
55. You are writing the technical specification for your solution. When a customer uses the new Web site to place an order, the new Web application must submit the order data to the accounting application. You need to specify how the data will be submitted. Which technology should you use?
Case Study
A. Transactional serviced component
B. .NET Remoting object
C. queued component
D. XML Web service
Answer: C
Going back to the 2 concurrent TCP/IP connections to the mainframe…. If Everyone hits the website at the same time… how will the solution cope if… for example a .Net remoting object was used ? If a queued component was used… that at least things wouldn’t get messy and the component would EVENTUALLY Be allowed a TCP/IP connection to the mainframe, once the other queued components have completed their tasks ! Basically… only 2 components can be connected (via a TCPClient object) to the mainframe at the same time. So… a queued component is the way to go (I think !).
A: Does the mainframe application support MSDTC using binary over TCP/IP ?! I don’t think so.
Slow + Locking (accounting application slow + only 2 channels - possible locking).
B: Not sure about B. It’s a toss between B and C… and I really think C is the way to go. But… then again… is a queued component a dot net Component or a COM component ?! If it’s a dot net component… then C… if its COM… then definitely B !!!?
D: This is not bad... But all customers will try to place orders at the end of month. Accounting application slow... We have really fast binary protocols over TCP/IP...
56. You need to select a user authentication mechanism for the new customer Web site. Which mechanism should you use?
Case Study
A. Basic Authentication
B. ASP.NET Forms authentication
C. Integrated authentication
D. ASP.NET Windows authentication
Answer: B
A: We need every user identified.
C: The users are not users in our network. They should be able to register themselves via web and login through a login form.
Just look at the ebay.com. Everyone welcome... If you want to buy something - log in...
Here's a useful guide on ASP.NET authentication: Source
57.

Case Study
A. Customer requests status -> Order is identified as open or complete -> Shipping status is retrieved -> Status is Presented
B. Customer requests status -> Shipping status is retreived -> Status is presented
C. Customer requests status -> Order total is calculated -> Shipping status is retreived -> Status is presented
Answer: B
58. You are writing the conceptual design for your solution. The Sales Manager sends you a spreadsheet containing sample data. Which new fact should you add to your conceptual design ?
Case Study
A. Standing orders are monthly, quarterly or annually
B. Customer has one standing order
C. Customer has a unique ID
D. Customer has several standing orders
Answer: C
A: only monthly
B: Customer MAY have one standing order
D: Customer may have ONE standing order
59. You need to ensure that the security implementation for the customer Web site meets the requirements of Fabrikam, Inc. Which strategy should you use?
Case Study
A. Use SSL to secure the logon page and customer order pages
B. Encrypt the customer category data and the product pricing data in the database
C. Encrypt only the customer category data in the database
D. Use SSL to secure only the logon page
Answer: A
You have to secure the logon (process of elimination as B and D are out)… and you need to secure credit card payment details that might be presented on the customer order pages !
60. You are designing the implementation of the interface to the accounting application. You need to ensure that the new application can communicate with the accounting application. What should you do?
Case Study
A. Create an XML Web service class
B. Create TcpClient objects
C. Create TcpListener objects
D. Create an XML Web service proxy class by using Wsdl.exe
Answer: B
Directly related to Q5. We are using .NET Remoting (via a queued component) in Q5, so we must use TcpClient to communicate with mainframe which already has TCP Listener.
61. You are planning the deployment of the new application. You need to decide how to migrate customer data on the shortest possible time. What should you do?
Case Study
A. Load the customer data into the new application from Active Directory.
B. Create a Data Transformation Services package to load the customer data into the new application from the mainframe computer.
C. Create an interface to the accounting application. Always access customer data from the accounting application.
D. Create a Data Transformation Services package to load the customer data into the new application from the customer category data.
Answer: B
A: Never heard about.
C: Accounting application is SLOW. There is ONLY two TCP/IP channels to communicate...
D: Where I can find customer category data. And also its CATEGORY data - not CUSTOMER.
Customer data would probably have to be expanded to include new fields (like login password if ASP.NET Forms Authentication is going to be used) but the existing customer data on the mainframe should not be modified otherwise there would be a need to make modifications to the Accounting Application on the mainframe which is what we need to avoid. DTS is the ideal tool for Data Migration.
Moreover - just say it again: "Accounting application is SLOW. There is ONLY two TCP/IP channels to communicate..."
62. You need to create a physical design that meets the monitoring requirements of Fabrikam, Inc. What should you do?
Case Study
A. Create and use a new event log to record each customer logon event.
B. Use the built-in ASP.NET performance counters to monitor application load.
C. Use the Trace class to record each customer logon event.
D. Create and use new NumberOfItems performance counters to monitor active customer sessions.
Answer: D
A: During peak loads, we must be able to monitor... Event Log - not a good place in this case. I'm not talking about quantity or records and size of log... Just imagine how you will calculate quantity of customers through peak hours...
B: ...how many customers in each customer category...
C: Tracing useful only at the development stage.
Guys, just carefully read question. We talking about monitoring requirements of Fabrikam, Inc. Going to case study: During peak loads, we must be able to monitor how many customers in each customer category are logged on to the site.
63. You are creating the physical design for the customer category data model. For reporting purposes, you want to optimize access to customer category data. You define a Customer table and a Category table. What should you do next?
Case Study
A. Define three foreign key columns in the Category table, such that each column references a different parent row in the Customer table. Define indexes on the foreign key columns.
B. Define three foreign key columns in the Customer table, such that each column references a different parent row in the Category table. Define indexes on the foreign key columns.
C. Define a foreign key column in the Category table that references the parent row in the Customer table. Define an index on the foreign key column.
D. Define a foreign key column in the Customer table that references the parent row in the Category table. Define an index on the foreign key column.
Answer: D

64. You are validating your physical design. You need to ensure that the design maps to the categorization requirements for customer pricing. Which member should you include in the design?
Case Study
A. A GetPrice method of a Product class with no parameters
B. A Price property of a Product class
C. A Price property of a Customer class
D. A GetPrice method of a Product class with a single Customer Object parameter
Answer: D
65. You need to recommend standard development processes for your solution. Your recommendations must assist the development team in learning to use the Microsoft :NET Framework as quickly as possible. Which process or processes should you recommend? (Choose all that apply)
Case Study
A. Create an automated build process
B. Install error-tracking software
C. Ensure that all assemblies pass unit testing
D. Permit individual developers to use any Microsoft .NET language
E. Hold regular code reviews
Answer: C, E
D: I don't think individual developers should be given that much freedom to decide on what language to use... probably better to adhere to some kind of standard and decide on the language as a whole development team. It would facilitate communication between team members. (eg, if you were the only member of the team coding in C#, you probably wouldn't be able to seek any help from your peers if another he/she decided to code in VB or J#). In this case, you might not be able to do (E).
66. You are writing the technical specification for your solution. What type of solution should it be.
Case Study
A. Thick Client
B. Web application
C. n-Tier
D. Console application
Answer: C
A: We need graphics.
B: This would be too hard to upgrade and maintain. We need to put much of the application on the branch servers.
D: We need to protect the kiosks operating systems.

We should use a 3-tier application.
The presentation layer will reside in the windows 2000 kiosks.
"The method of navigation must prevent children from accessing the features of the operating system."
We need a program that is similar to what we will use to take this test.
The business logic layer will reside in each of the branches IIS.
The data layer (for the reporting requirements) will reside in a server
67. You are listing the requirements for the Baldwin Museum of Science. Which requirement or requirements should you include? (Choose all that apply)
Case Study
A. Maintainability
B. Ease of use
C. Extensibility
D. Performance
Answer: A, B, C, D
A: "....It should require the minimum of administrative effort"..... this is a maintainability requirement. B: Online help in a format that is comfortable for children and easy for them to use
C: We must be able to reuse modules easily. Whenever a module is upgraded, all of our applications must be able to take advantage of upgrades in every module
D: Highly interactive operation, with fast response time and immediate feedback to users
68. You are assessing the impact of your solution on the existing IT environment. You decide that the environment needs to be modified. What should you do?
Case Study
A. Upgrade Internet Explorer to version 6.0.
B. Upgrade the kiosk computers to Microsoft Windows XP Professional.
C. Increase bandwidth between the museum branches.
D. Add more space to the hard disks of the servers.
Answer: C
C: We need to shut down the kiosk computers all day for this update. The Connection is too slow(56k).
“We plan to install a dedicated streaming media server at the main branch of the museum”
…they are referring to Windows Media Server and Microsoft Content Management Server.
Extract from windows media service documentation:
“For large-scale deployments of Windows Media Services, try making one or more of the following modifications to your streaming media system:
• Upgrade from a single-CPU server to a multiple-CPU server.
• Install additional network interface cards, or upgrade the existing network interface card to support a higher bandwidth network connection.
• Add additional servers running Windows Media Services to your streaming media system and use Network Load Balancing to distribute the server load.
• Distribute cache/proxy servers throughout the network and implement a content replication program to distribute content closer to the clients and relieve some of the demand on the origin servers.
• Set the network switches that will be processing streaming media requests and transmissions to full duplex mode to maintain an uninterrupted information flow. “ located in the main branch. "
69. You need to provide user assistance for your exploration applications. What should you do?
Case Study
A. Add context-sensitive help to all screen elements.
B. Add pop-up text for all screen elements.
C. Add an interactive animated character that talks to the user.
D. Create a streaming media tutorial for each application.
Answer: C
C: Online help in a format that is comfortable for children and easy for them to use
70. You are designing a common interface for launching your exploration applications. What should you do?
Case Study
A. Create a multiple-document interface (MDI) application.
List the available exploration activities on the View menu.
B. Launch each application in a separate MDI window.
C. Create an application that displays a graphical image of each exploration activity in the application window.
When the user clicks an image, launch the appropriate application.
D. Create a single-document interface (SDI) application.
List the available exploration activities on the View menu.
Switch applications within the SDI window.
E. Create shortcuts for each exploration activity.
Place the shortcuts on the desktop.
When the user clicks a shortcut, launch the appropriate application.
Answer: C
C: Graphical format is easy for kinds to understand and use ! Bear in mind... they might not even be able to read yet !
"Easy navigation between exploration applications.
The method of navigation must run continuously.
The method of navigation must prevent children from accessing the features of the operating system.
The method of navigation must prevent children from stopping its execution.
Support for children with special needs, such as low vision or hearing disabilities."
A: We do not list the available exploration activities in the view menu.
B: We don't need a separate MDI for each application.
D: We need to use something more intuitive. How will they know how to switch applications.
E: We should not give the user access to the desktop.
We need to use something more intuitive. How will they know about the shortcut.
71. The navigation application will be used to access all of your exploration applications. You are creating a conceptual model for this application. Which object or objects should you model? (Choose all that apply)
Case Study
A. Title bar
B. Main screen
C. Logon Manager
D. Animated assistant
Answer: B, D
A: The title bar is a property of the window that is opened.
C: The Logon Manager will not be part of the navigation application.
B: This is the Main screen where they click on the graphical image of the exploration activity that they want to launch (see Q5)
D: This object provides animated help
72. You are designing the methodology for installing and upgrading your exploration applications and their shared assemblies. Your methodology should support new applications and updates to existing applications. It should require the minimum of administrative effort.
Which two strategies should you use? (Each correct answer presents part of the solution. Choose two)
Case Study
A. Install all applications in the same directory as the navigation application.
B. Install the shared modules in the \bin directory of each application.
C. Install each application in the application \bin directory of Inetpub\wwwroot.
D. Install the shared modules in the global assembly cache (GAC).
E. Install each application in a separate application directory.
Answer: A, D
A: Minimum admin effort. Less virtual directory to create and administer.
D: Whenever a module is upgraded, all of our applications must be able to take advantage of upgrades in every module
73. You are designing an assembly to monitor the usage of your exploration applications. Reports that describe usage will be generated at the main branch of the museum. You need to select a strategy for logging the appropriate information.
What should you do?
Case Study
A. Add a TextWriterTraceListener to the Listeners collection to write an entry each time an application is started.
B. Create a System.Diagnostics.EventLog to write an entry each time an application is stated.
C. Use the System.Diagnostics.TraceSwitch to write an entry each time an application is started.
D. Use the System.Diagnistics.Debug.WriteLine to write an entry each time an application is started.
Answer: A
A: You need to generate a report, so writing to a text file is better. Extracting info from EventLog is cumbersome.
74. The online store application needs to be localized. You plan to use the localization support in the Microsoft .NET Framework. Which localization feature or features are feasible? (Choose all that apply)
Case Study
A. Support multiple character sets (MBCS).
B. Support right-to-left mirroring of Web pages.
C. Automatically translate text for different cultures.
D. Automatically convert currency values for different cultures.
E. Support localized resources for different cultures.
F. Automatically format currency for different cultures.
Answer: E, F
A: This is C++ feature. We talking about feasible features. Right?
B: The .NET Framework does not support mirroring Source
C, D: The .NET Framework does not support text translation or currency conversion. But it can be implemented by XML Web Services...
75.

Case Study
A. Phase I
Develop a single sign-on module.
Develop one or more applications to update product data.
Devolop a module that will replace the terminal emulation software.
Phase II
Develop a local-aware version of the online store application.
B. Phase I
Develop one ore more applications to update product data
Develop a module that will replace terminal emulation software
Develop a local-aware version of the online store applicaiton
Phase II
Develop a single sign-on module.
Develop application to translate product data into multiple languages.
C. Phase I
Develop a single sign-on module
Develop one or more application to update product data.
Develop a module taht will replace terminal emulation software
Develop application to translate product data into multiple languages.
Phase II
Develop a local-aware version of the online store application.
Answer: A
"Develop an application to translate product data into multiple languages" - is that required at all?
The business process specifies: "Each tape provides product names and descriptions in several different languages".
If we have already got the data in different languages why should we write code to translate it?
Phase 1 needs to address all these issues as the background states that the worldwide deployment must be completed without any additional development effort.
Phase 2 because the pilot implementation does not include worldwide deployment.
76. You need to identify the primary actors who will participate in the use cases for the online store application. Which type of actor should you identify?
Case Study
A. Delivery truck driver at a distribution centre.
B. Inventory management clerk at a distribution centre.
C. Customer.
D. Accountant.
Answer: C
http://www.objectsbydesign.com/books/larman_notes/2-RequirementsModeling.html
77. The company’s inventory management application runs on a mainframe computer. You are creating the functional specification for a new Web application that will provide access to this application. You propose the use of Microsoft Host Integration Server. Which requirement or requirements will Host Integration Server meet? (Choose all that apply)
Case Study
A. Web-based access to the inventory management application.
B. Single user logon to a desktop computer and the mainframe computer.
C. Secure connectivity through the internet.
D. Ability to print mainframe computer reports.
Answer: A, B, C, D
A: Host Integration Server provides ActiveX-enabled 3270 and 5250 clients.
B: Host Integration Server provides Single User Log-On which streamline and reduces management burden by automatically and simultaneously authenticating a user on both the Windows NT domain and on the host system.
C: With Host Integration Server, you have secure, low-cost tunneled connectivity through the Internet for client-to-server and network-to-network VPN features.
D: Host Integration Server 2000 has a Host Print Service which provides server-based 3270 and 5250 print emulation, allowing mainframe and AS/400 applications to print to a LAN printer supported by Windows 2000 and Windows NT Servers. Host Print Service
HIS features
78. After the online store is implemented, vendors will use data files instead of tape to deliver product update data. However, each vendor uses a different file format. Input files need to be processed to produce output files in a standard format. Output files will be submitted to the mainframe computer. You need to recommend a flexible solution for file processing. What should you do?
Case Study
A. Create a Windows service that periodically examines a folder for new files and processes them.
B. Use Microsoft Host Integration Server.
C. Create a console application.
D. Use Microsoft Biz Talk Server.
Answer: D
Microsoft BizTalk Server is designed for this.
It has Data and transformation services and the application integration features in BizTalk Server can provide businesses with the tools they need to achieve a unified view of data and applications both within the organization and business partners. Refer to the Product Overview.
79. Your development team is creating the conceptual model of an order. You need to comply with the following business rules.
* Each order must have at least one LineItem
* Each LineItem must have only one product
Your team proposes four different Object Role Modeling (ORM) diagrams. Which diagram should you use?
Case Study
A.

B.

C.

D.

Answer: D
http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dv_vstechart/html/vstchvseamodelingp1.asp
http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dv_vstechart/html/vstchvseamodelingp2.asp
http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dv_vstechart/html/vstchvseamodelingp3.asp
http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dv_vstechart/html/vstchvseamodelingp4.asp
http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dv_vstechart/html/vstchvseamodelingp5.asp
This is the explanation for Answer C using Visio:

This is the explanation for Answer D using Visio :

... come to your own conclusion.
80. You create a product fact diagram to explain your solution. Which fact or facts does the diagram show? (Choose all that apply)
Case Study
A. A unique index will be created over the Product Role.
B. Each Product has at most one vendor.
C. Every product is identified by one distinct ProductID.
D. It is possible that some Products have more than one Vendor.
E. A unique index will be created over the Vendor Role.
Answer: B, C
81. You are creating the logical design for customer profiles. These profiles contain data that requires the highest possible level of security. Which strategy or strategies should you recommend? (Choose all that apply)
Case Study
A. Log all failed customer logon attempts.
B. Lock out a customer after a predefined number of failed logon attempts.
C. Encrypt all confidential customer information.
D. Authenticate each customer by using a logon process.
Answer: B, C, D
A: Although in practice failed customer logon attempts should be logged, it does not increase security.
82. You are creating the data model for a table named Product. This table will contain data relating to products sold by Northwind Traders. Each product can belong to more than one category. Categories include furniture, bedding, bath accessories and kitchen goods. Which entity or entities should you model?
Case Study
A. A Product entity that contains attributes for three Category names and descriptions.
B. A Product entity and a Category entity that are related by a ProductID attribute.
C. A Product entity and a Category entity that are related by a ProductID attribute and a CategoryID attribute.
D. A Product entity, a Category entity and a ProductCategory entity that are related by a ProductID attribute and a CategoryID attribute.
Answer: D
There is a Many-to-Many relationship between Product and Category but some Relational DBMS (including SQL Server) can't do Many-to-Many relations. This would require an additional ProductCategory entity.
83. You are creating the logical design for the online store application. You are retrieving a use case named "Customer places an order item in the virtual shopping cart". Which object or objects should you include to support the use case? (Choose all that apply)
Case Study
A. Transaction object
B. Virtual Shopping Cart object
C. Order Item object
D. Customer object
Answer: B, C, D
84. You need to deploy a new Web application that will enable employees to access the mainframe computer. You plan to use the services provided by Microsoft Host Integration Server. What should you do?
Case Study
A. Add an OBJECT tag with a CODEBASE attribute to the Web page for the ActiveX controls for Host Integration Server.
B. Create a Windows Installer package and install the package on the desktop computers used by the employees.
C. Use a group policy object (GPO) to advertise the application on the Start menu of the desktop computers used by the employees.
D. Use XCOPY to distribute the components to the desktop computers used by the employees.
Answer: A
C: It's a Web-application. OBJECT tag will be more appropriate.
Just think about Java applets... Source
85. You are creating the physical design for a database table that will contain product information. Your design must support multiple translations of the ProductName entity and the ProductDescription entity. You evaluate four different designs. Which design should you use?
Case Study
A.

B.
C.
D.
Answer: A
This one is easy. We have one Product definition and multiply translations + unit prices.
86. You must enable the marketing department to analyze data that relates to virtual shopping carts. Which action or actions should you take? (Choose all that apply)
Case Study
A. Create an OLAP interface to the mainframe computer to enable the marketing department to perform its analysis
B. Create OLAP cubes by using Analysis Services
C. Use Microsoft Excel and Pivot Table Services to enable the marketing department to perform its analysis
D. Use Data Transformation Services (DTS) to extract customer demographic information and order information to a Microsoft SQL Server computer at the main office
E. Use Microsoft SQL Server Replication to copy the customer demographic information and order information to a SQL Server computer at the main office
Answer: B, C, D
A: The DBMS on the mainframe computer probably does not support OLAP Cubes.
E: Replication is not used to copy data from the mainframe to SQL Server.
B: To use Pivot tables, you need a connection to an OLAP Cube which is provided by Analysis Servers in Microsoft SQL Server.
C: Employee desktop computers have Office XP installed, so they can use Microsoft Excel and Pivot Table Services to perform its analysis.
D: You need to import the data into Microsoft SQL Server using DTS.
OLAP Cubes
Processing Objects Using Data Transformation Services
OLAP, DataGrid, and Ann Landers
87. You want to establish development process that will speed the detection of development errors. Which two processes should you recommend?( Each correct answer presents part of the solution)
Case Study
A. Daily integration testing.
B. Daily validation of application build.
C. Daily build of application code.
D. Daily system testing.
E. Daily code reviews.
Answer: B, C
A: A lot of effort.
A: Integration testing is a logical extension of unit testing. In its simplest form, two units that have already been tested are combined into a component and the interface between them is tested. A component, in this sense, refers to an integrated aggregate of more than one unit. In a realistic scenario, many units are combined into components, which are in turn aggregated into even larger parts of the program. The idea is to test combinations of pieces and eventually expand the process to test your modules with those of other groups. Eventually all the modules making up a process are tested together. Beyond that, if the program is composed of more than one process, they should be tested in pairs rather than all at once.
E: I don't think that is practical. Code being reviewed every day even if it is half finished. That sounds to me like a huge investment of resources for very little gain.
C: Daily validation of the build - it is just having someone look at the output from the build and see if there are any warnings or errors that need to be addressed.
88. You are establishing a new development environment for the online store application. You are using source code control (SCC) software. Every night, you must perform software builds that use the source code currently in SCC. Which action or actions should you take? (Choose all that apply)
Case Study
A. Copy the most current source code from SCC onto the lead developer’s computer.
B. Check all source code into SCC every night.
C. Check all source code into SCC after unit testing.
D. Copy the most current source code from SCC onto an isolated build computer.
Answer: C, D
C: Your should only check in source code in SCC after it has been tested.
D: As the question states, you must perform software builds that use the source currently in SCC, so it's good practice to copy the source code onto an isolated build computer.
89. You must minimize the time required to establish whether a course section is fully enrolled. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two)
Case Study
A. Keep a hash table of enrolment counts for each course section. Save the hash table in the ASP.NET Cache object.
B. Keep a hash table of enrolment counts for each course section. Save the hash table in the ASP.NET Application object.
C. Create an index on the CourseSectionID foreign key column in the StudentCourseSection table.
D. Denormalize the course registration database so that the CourseSection table contains a column for enrolment count.
Answer: C, D
B: To keep application data in sync across web farms is going to be painful. Plus... no session affinity must be allowed on the web servers
D: Creating a denormalized field on the CourseSection table (e.g. called CoursesEnrolledSoFarCount) would DEFINITELY speed things up when wanting to find out if the course section is fully enrolled or not.
C: As each correct answer presents part of the solution, C is the next obvious answer. To create the CoursesEnrolledSoFarCount field, you would need to run the following query against the StudentCourseSection Table.

SELECT @CoursesEnrolledSoFarCount = count(*)
FROM StudentCourseSection
WHERE CourseSectionID = ?
The index on the CourseSectionID will SPEED up the query and you'll be able to determine the results almost instantly (as opposed to a table scan being run - ouch ! Slow !).
90. The Web application for the student registration includes business logic that queries TRANS2. The purpose of the query is to establish whether a student satisfies the prerequisite requirements for a course. Preliminary testing shows that the query is slow. To optimize access to transcript data, you need to minimize the number of these queries. What should you do?
Case Study
A. Store the student’s transcript data in the ASP.NET Session object. Use the default session state configuration
B. Cache the students transcript data in a session cookie.
C. Use ASP.NET page caching
D. Store the student’s transcript data in the ASP.NET Session object. Configure ASP.NET to store session state in a Microsoft SQL Server database
Answer: D
A: This is considered in-process storage where information that is added to a session state is stored in the same web server. This is not scalable.
B: Client side caching of cookies will not improve query performance on the server.
C: ASP.NET caching is also a possible option, but maximum scalability and flexibility is what's needed here.
IT Manager wants scalability and flexibility and does not want any web server session affinity. Using an out-of-process storage to store session state (i.e., SQL Server or separate State Server) will make the web application scalable as session variables can be retrieved from any server of a web farm since the session state is stored on a separate server.
91. You want to simplify the code that embodies security restrictions and exception handling. You also want to minimize redundant code. What should you do?
Case Study
A. Use Microsoft Visual Studio .NET Enterprise templates.
B. Use Microsoft .NET reflection.
C. Derive all classes in your solution from a single base class that implements best practices.
D. Apply attributes.
E. Use utility components.
Answer: C
Enterprise Templates quickly get you building distributed applications by providing a choice of customized architecture models that fit your company's application infrastructure.
The policy file of an application template describes the elements of a multiproject application and the technologies to build it. Policies can permit specific components, references, or controls and exclude others. They can shape elements and their properties and can customize the Visual Studio environment to meet the needs of team members and projects.
Just carefully read question:
You want to simplify the code that embodies security restrictions and exception handling.
We not talking about controls, components or references... So, right answer - C
See also : The Dwarmish7 sample that comes with the Microsoft .Net Framework Installation. They use a base class for every module and every page !
92. Your developers are allowed to use only the project types and components that are approved by your architectural guidance team. You need to establish a process to ensure that the developers comply with this guideline. This process should be as automatic as possible. What should you do?
Case Study
A. Create and distribute a Microsoft Visual Studio .NET Enterprise template
B. Use Enterprise Services components
C. Establish a code review process
D. Write and distribute a white paper detailing your architectural policies
Answer: A
(See A. Datum Corporation.html Q14)
Enterprise Templates help define policies and best practices that simplify the Visual Studio integrated development environment (IDE) and offer guidance throughout the development process. You can refer to this URL.
93. Which new module or modules should you develop for the school of Fine Arts? (Choose all that apply)
Case Study
A. An accounting database
B. A Web application for administrators, academic counsellors and professors
C. A course registration database
D. An application to report transcripts
E. A Web application for student registration
F. A utility to export course registration data
Answer: B, C, E, F
94. You are creating a list of business requirements for your solution. Which two requirements should you include? (Each correct answer presents part of the solution. Choose two)
Case Study
A. A professor can grant a student a waiver from a prerequisite requirement for any course section
B. A professor can grant a student a waiver from a prerequisite requirement for any course section that he or she teaches
C. An academic counsellor can grant a student a waiver from a prerequisite requirement for any course section
D. An academic counsellor can grant a student a waiver to enrol in a course section even if it is fully enrolled
Answer: B, C
A: A professor can only grant waivers for the course section that he/she teaches.
C: Only professors, not academic counsellors, can grant a student a waiver to enrol in a course section even if it is fully enrolled.
These were specified by the Director, Department of South Asian Art.
95. You are writing the functional specification for your solution. You need to specify the data integration needs and the migration needs for transferring data to and from the existing REG2 and TRANS2 databases. Which two statements should you include in your specification? (Each correct answer presents part of the solution. Choose two)
Case Study
A. The new student registration application must query historical transcript data in REG2.
B. Student data, professor data and course schedule data from REG2 are needed to initially populate a Microsoft SQL Server course registration database.
C. Student data, professor data and course schedule data from REG2 will be needed each term to populate the Microsoft SQL Server course registration database.
D. The new student registration application must query historical transcript data in TRANS2.
Answer: B, D
A: REG2 does not contain historical transcript data.
C: This is the opposite of (B).
B: This is what the AS/400 Application Support Engineer says.
D: Historical transcript data is in TRANS2.
96. You are writing the technical specification for your solution. You need to implement a class that will retrieve information about tuition account status from the Accounting database. Which implementation should you specify?
Case Study
A. A queued component
B. A Microsoft .NET serviced component that requires a transaction
C. A Microsoft .NET class that is not a serviced component
D. An XML Web service proxy class
Answer: C
Since information is retrieved, it is not necessary to use a serviced component that requires a transaction (not B).
97. You are writing the technical specification for your solution. You need to implement a class that will update information about course credit in the Accounting database. Which implementation should you specify?
Case Study
A. A queued component
B. A Microsoft .NET serviced component that requires a transaction
C. A Microsoft .NET class that is not a serviced component
D. An XML Web service proxy class
Answer: B
Accounting is an Oracle database which has on OLE DB provider and supports Microsoft Distributed Transaction Coordinator. When updating information, it is better to use transactions.
98. You are using Object Role Modelling (ORM) to model data relationships between courses and course sections. You plan to use entities named Course and CourseSection. Which fact should you include in your model?
Case Study
A. CourseSection has a name.
B. It is possible that the same CourseSection is of more than one Course and that the same Course has more than one CourseSection.
C. Course has CourseSection. CourseSection is of Course.
D. Course has a location.
Answer: C
A: We only care about course name.
B: I don't think that in ORM you will use sentences like "It is possible..."
D: CourseSection has a location. Sometimes...
99.

Case Study
A. Student seclects Course for which to register
Application queries ReG2 to verify that the course is not fully enrolled.
Application queries REG2 for prerequisite requirements and then queries TRANS2 to verify that requirements are met
Application updates course credits in the Accounting database
Application registers student in course
B. Student seclects Course for which to register
Application queries REG2 for prerequisite requirements and then queries TRANS2 to verify that requirements are met
Application queries ReG2 to verify that the course is not fully enrolled.
Application registers student in course
Application updates course credits in the Accounting database
C. Student selects course for which to register
Application queries REG2 to verify that the course is not fully enrolled
Application queries REG2 for prerequisite requirements and then queries TRANS2 to verify that requirements are met
Application registers student for any prerequisites that are unmet
Application updates course credits in the Accounting database
Application registers student in course
D. Student selects course for which to register
Application queries ReG2 to verify that the course is not fully enrolled.
Application queries REG2 for prerequisite requirements and then queries TRANS2 to verify that requirements are met
Application updates course credits in the Accounting database
Application registers student in course
Application exports course enrolment data in an XML text file
Answer: A
At the end of each registration period, we must be able to import into TRANS2 a list of all courses for which a student is registered.
Each registration period begins one month before the beginning of an academic term. Registration closes when the term begins. A summary of student enrolment data is then exported by a batch export operation from REG2 to TRANS2.
Application should update course credits in the Accounting database before registers student in course - We want to make it impossible for students with overdue tuition accounts to register for courses.
100. You need to identify the sequence of decisions that are required when a student tries to register for a course section. Proposed sequences are shown in the sequence diagrams. Which diagram should you use?
Case Study
A.

B.

C.

D.

Answer: A
B: With this diagram, even if the course is full, it is possible for the student to have a waiver from an Academic counsellor ! This is incorrect ! A student can't register for a fully enrolled course with a waver from an Academic counsellor.
C: An Academic counsellors cannot issue a waiver if the course if full
D: The course must be checked to see if its full 1st. Not check if the student meets the prerequisites !
101. To create the logical data model for your solution, you need to identify the relationships between the Student, Course and CourseSection entities. Which two entity relationships should you identify? (Each correct answer presents part of the solution. Choose two)
Case Study
A. There is a many-to-many relationship between the Course entity and the CourseSection entity
B. There is a many-to-many relationship between the Course entity and the Student entity
C. The Course entity is a parent of the CourseSection entity
D. The Student entity is a parent of the CourseSection entity
E. There is a many-to-many relationship between the CourseSection entity and the Student entity
F. The Student entity is a parent of the Course entity
Answer: C, E
A: The should be a One-to-Many relationship between Course and CourseSection.
D: Course (not Student) should be the parent of CourseSection.

102. The new administrative application will be used by administrators, professors and academic counsellors. You need to select a mechanism that will authorize the use of application functionality on the basis of user type. Which mechanism should you use?
Case Study
A. Access Control List (ACL) based security.
B. Integrated Windows authentication.
C. Microsoft .NET role-based security.
D. Code access security.
Answer: C
B: This is a possible answer but there is no indication that all administrators, professors and academic counsellors have Windows login accounts.
D: Code access security allows code to be trusted to varying degrees, depending on where the code originates and on other aspects of the code's identity.
Code access security also enforces the varying levels of trust on code, which minimizes the amount of code that must be fully trusted in order to run. Using code access security can reduce the likelihood that your code can be misused by malicious or error-filled code. It can reduce your liability because you can specify the set of operations your code should be allowed to perform as well as the operations your code should never be allowed to perform. Code access security can also help minimize the damage that can result from security vulnerabilities in your code. Source. This is not what we want here.
This will allow the use of application functionality on the basis of user type. Role-based security supports authorization by making information about the principal, which is constructed from an associated identity, available to the current thread. The identity (and the principal it helps to define) can be either based on a Windows account or be a custom identity unrelated to a Windows account. Source
103. You are creating the physical design of the Web application for student registration. Your design includes a Web page that shows all course names within a selected department. The content of this page will change once each term. The page is generated slowly. You want to optimize its generation. What should you do?
Case Study
A. Store the list of courses for each department in a session cookie
B. Store the list of courses for each department in the ASP.NET Application object
C. Store the list of courses for each department in the ASP.NET Session object
D. Use ASP.NET page caching
Answer: D
A: Session cookies are stored on the client and lost when the browser is closed, so it's definitely not going to do any good here.
B: Caching the course names at the application level can be efficient, but there's little automatic control over when the data is refreshed.
C: Caching the course names at the session level can be efficient, but there's little automatic control over when the data is refreshed.
ASP.NET provides two types of caching that you can use to create high-performance Web applications. The first is called output caching, which allows you to store dynamic page and user control responses on any HTTP 1.1 cache-capable device in the output stream, from the originating server to the requesting browser. On subsequent requests, the page or user control code is not executed; the cached output is used to satisfy the request. The second type of caching is traditional application data caching, which you can use to programmatically store arbitrary objects, such as data sets, to server memory so that your application can save the time and resources it takes to recreate them. Source
104. You are designing a utility to export all data from REG2 to an XML file. The utility must write important messages to an event log. You must choose a log type. What are two possible log types for you to use? (Each correct answer presents a complete solution. Choose two)
Case Study
A. The Application log
B. The System log
C. The Security log
D. A Custom log
Answer: A, D
Applications and services should add their names to the Application log file, or a custom log file. Device drivers should add their names to the System log file. The Security log file is for system use only. Source
105. You are validating the logical data model for course prerequisites. Which two entity relationships should be included. (Each correct answer presents a complete solution)
Case Study
A. Prerequisite entity is a parent of Course entity.
B. PrerequisiteCombination entity is a child of Course entity.
C. PrerequisiteCombination is a parent of Course entity.
D. Prerequisite entity is a child of PrerequisiteCombination entity.
E. Prerequisite entity is a child of Course entity.
Answer: B, E
A: Prerequisite entity is a child of Course entity
C: PrerequisiteCombination entity is a child of Course entity
D: Our existing scheduling application lets us specify prerequisite courses only in a very simple way.
Note… remember, When they speak about an entity… they’re talking at a TABLE level, not about a column within a table.
All the combinations for a course are setup within the PrerequisiteCombination Table. So in our example, Course 4 (ARTHI 303) has 2 combinations.
These combinations are defined within the Prerequisites Table.
Combo 1 consists of doing course 1 (ARTHI 101) and course 2 (ARTHI 202).
Combo 2 consists of doing course 3 (ARTHI 301)

106. You need to develop two business layer classes that will be used by the IVR application. The IVR application will be complete in two weeks. Your business layer classes will be complete in six weeks. You need to manage these conflicting development schedules and minimize integration time. What should you do?
Case Study
A. Instruct the IVR consultant to comment out the IVR application code that references the classes that you will create
B. Instruct the IVR consultant to create classes that are equivalent to the classes that you will create
C. Create and document the database. Then instruct the IVR consultant to access the database directly instead of using your classes
D. Create skeleton classes or interfaces for the IVR consultant to use
Answer: D
A, B: This is not his problem.
C: It's completely wrong.
107. You create a prototype Web page for the Web application used by supervisors, as shown in the exhibit. The Web page displays a summary of a driver-s program compliance and drug test results, ordered by date. You need to modify the page to display the required information in a way that emphasizes instances of non-compliance. What should you do?
Case Study
A. Modify the Web page to show all days when the driver telephoned
B. Remove the test results summary
C. Modify the Web page to show all drivers
D. Modify the Web page to show all days when the driver did not telephone
Answer: D
108. You need to design a deployment mechanism for the Web application used by supervisors. This application includes components that need to be installed in the global assembly cache (GAC). The deployment mechanism must require a minimum of development effort. What should you do?
Case Study
A. Create and use a Setup project
B. Create and use a Web Setup project
C. Copy files from the target folder of your build server
D. Use an XCOPY deployment
Answer: B
109. The OCR software receives a fax, converts it into a text file and writes the file in a designated folder. You need to create a module that automatically imports laboratory data from this folder. The module must be able to start when its host computer starts, without requiring a user to log on. Which type of module should you create?
Case Study
A. An XML Web service
B. A serviced component
C. A console application
D. A Windows service
Answer: D
110. You are writing the technical specification for your solution. You need to specify the most appropriate and secure authentication mechanism for the Web application used by supervisors. Which authentication mechanism should you specify?
Case Study
A. ISS Basic Authentication with SSL and Windows authentication mode in ASP.NET
B. ISS Basic Authentication with SSL and no ASP.NET authentication
C. ISS Integrated Windows Authentication with Windows authentication mode in ASP.NET
D. ISS Anonymous Authentication with SSL and Forms authentication mode in ASP.NET
Answer: D
A, B, C: Incorrect. These do not provide the most appropriate and secure authentication.
Trucking supervisors will need to provide a user name and a password to access the web application. Because drug-testing information is highly confidential, all information must be transmitted securely.
By using IIS's anonymous authentication in conjunction with ASP.NET Forms Authentication, we create a highly secure, highly scalable application that meets all of the case's requirements, without the added hassle of Windows Domain account administration.
You should consider Integrated Windows authentication when:
• Your users have Windows NT Domain or Active Directory accounts.
• Your application runs on an intranet (behind a firewall).
• All of your clients are running Internet Explorer version 3.01 or later.
• You need to perform delegation (this require s Kerberos).
• You need a seamless logon procedure for domain users (for example, without pop-up logon dialog boxes).
You should not consider Integrated Windows authentication when:
• Your user accounts are stored in an external database rather than a Windows NT Domain database or Active Directory.
• You need to support authentication over the Internet.
• Your clients are using Netscape Navigator or other non-Microsoft browsers.
• You need to obtain the client's clear text password. "
111. You are writing the functional specification for your solution. You need to specify the security requirements of the Web application used by trucking supervisors. Which statement or statements should you include? (Choose all that apply)
Case Study
A. Drivers who are not trucking supervisors must use their assigned identifier to log on to use the supervisor Web application
B. Logon information must be transmitted securely over the internet
C. Trucking supervisors must log on to use the supervisor Web application
D. Driver information, including drug test results, must be transmitted securely over the internet
E. After they log on, trucking supervisors are authorized to view all drivers who are currently on probation
Answer: B, C, D
112. We just received txt-file from OCR-application into some local folder. What is the right sequence of operations for saving this information in the database?
Case Study
Possible Actions:
Open txt-file
Archive txt-file
Create new Driver
create new Supervisor
Create Drug Results
Get Driver info (name, ...)
Get Drug results from Laboratory
Ordered Actions:
A. Open txt-file
Get Driver info (name, ...)
Get Drug results from Laboratory
Create new Driver
Create new Drug Results
Create new Supervisor
B. Open txt-file
Get Driver info (name, ...)
Create new Driver
Create new Supervisor
Create new Drug Results
Get Drug results from Laboratory
C. Open txt-file
Create new Driver
Create new Supervisor
Get Driver info (name, ...)
Create new Drug Results
Get Drug Results from laboratory
Answer: A
113. You are writing a conceptual diagram of the modules that must be developed for your solution. Which module or modules should be included? (Choose all that apply)
Case Study
A. OCR-application
B. Web-app for supervisors
C. Web-app for drivers
D. Module for export Lab results
E. Module for import Lab results
F. Database
Answer: B, C, E, F
114. Which things poses the greatest potential risk to completing your project?
Case Study
A. Stuff don't have programming experience
B. App will be hosted by Trey Research
C. IVR application
D. Nobody will want to use this application
E. Drivers will not call
Answer: C
115. How often drivers will be testing?
Case Study
A. Decided by company
B. Decided by driver
C. Will be set up by supervisor once for all companies and drivers
D. ...
Answer: A
The key to random drug testing is surprise.
116. Substance table (parent) - Lab Result table (child). How you can speed up process of getting Lab results?
Case Study
A. Create PK in Lab Results and index
B. Create FK + index in Lab Results
C. Create FK + index in Substance
D. ...
E. ...
F. ...
Answer: B
117. You need to include two key project risks in your risk assessment plan. Which two risks should you include ? (Each correct answer presents part of the solution. Choose two)
Case Study
A. The application might be hosted offsite
B. Users might be unwilling to use the IVR application
C. The project timeline might change
D. The IT staff has no programming experience
E. Laboratories have no on-site IT support
F. Communication and coordination issues might develop with an independent IVR consultant
Answer: C, F
C: If the merger negotiations continue, we want the pilot program to begin sooner
118. You need to present a list of potential project risks to the IT Manage of Woodgrove Bank. Which three potential risks should you include? (Each correct answer presents part of the solution. Choose three.)
Case Study
A. The loan department staff will not know how to use the new loan processing application effectively by the project deadline.
B. You will not be able to develop and appropriate interface with the applications that reside on Main1.
C. You will have difficulty to develop an appropriate interface with the applications that reside on Main1.
D. You will have difficulty selecting a database management system.
E. Your development staff lacks the expected level of experience.
F. You have difficulty selecting a development environment.
Answer: A, C, E
119. Which network protocol or protocols are required for your solution? (Choose all that apply.)
Case Study
A. NetBEUI
B. HTTP
C. DCOM
D. SNMP
E. HTTPS
Answer: B, C, E
Wrong Answers:
D: This is not needed. SNMP (Simple Network Management Protocol) is the Internet standard protocol for exchanging management information between management console applications. The managed entities can include hosts, routers, bridges, and hubs.
A: The current network supports TCP/IP and NETBEUI. Although I'm not comfortable with this answer, TCP/IP is not listed as an answer here.
C: Need a reliable interface between the new application and Main1. The interface must support transaction recovery and logging.
E: Loan request contain confidential information.
120. Your solution requires an interface between the new loan processing application and the applications that reside on Main1. You need to supply the specifications for a software product that will provide an appropriate interface.
Which three specifications should you supply? (Each correct answer presents part of the solution. Choose three.)
Case Study
A. Transaction recovery.
B. Support for workflow data exchange.
C. Integration with a data warehouse.
D. Transaction auditing and logging.
E. Reliable exchange of data between applications.
F. E-mail exchange of transaction history.
Answer: A, D, E
B, C, F: Not a requirement.
A: IT Manager- "The interface must support transaction Recovery and logging.".
D: IT Manager- "The interface must support transaction Recovery and logging.". Chief Financial Officer: "The new loan processing application must include an audit module.".
E: IT Manager- "we need a reliable interface between the new application and Main1".
121. High confidential applicant data is stored with each loan request. Your solution must ensure the security of this data. Which three security techniques should you recommend? (Each correct answer presents part of the solution. Choose three.)
Case Study
A. Authentication of application server components to the database management system.
B. Algorithmic validation of data fields.
C. Secure communications for loan requests from the Internet.
D. Password authentication for loan applicants.
E. Encrypted database fields.
F. Digital certificate authentication for loan applicants.
Answer: A, C, D
A: IT Manager- "The information must remain secure even if our firewall is penetrated.".
C: Loan requests contain confidential information.
D: IT Manager- "The confidential information that resides on this server must be inaccessible to unauthorized users.".
E: IT Manager - We need to keep the database secure even if the firewall is penetrated. However, encrypted database fields is not an SQL Server option. We have to use other means.
122. You need to recommend a strategy for storing the data associated with the loan processing application. Which strategy should you recommend?
Case Study
A. Install a new database on a new database server.
B. Use the local file system on the application server.
C. Use the existing database and database server.
D. Install a new database management system on the application server.
Answer: C
IT Manager: "Database1 will be used in the implementation of the new application.".
123. The conceptual database design for your solution requires validation. You need to use the most effective strategy for ensuring that all necessary data elements are included in your design. Which strategy should you use?
Case Study
A. Create the table definitions.
B. Review the use cases for data requirements.
C. Develop detailed test cases.
D. Create a representation of the data elements in third-normal form.
Answer: B
MSF recommends validating the conceptual database design against the use cases, usage scenarios, business requirements, architecture, risks, available resources and time, and all other artefacts that you have developed. This was extracted from MOC 2710A (Module 4).
124. You need to implement the presentation tier of the loan processing application.
Which technology or technologies should you use? (Choose all that apply.)
Case Study
A. IIS
B. ADO.NET
C. XML Web services
D. Secure sockets
E. ASP.NET
Answer: A, D, E
Not B (this would exist within a data component on the Business Logic tier !!!) and not C (as there is no need for an XML Web Service).
A: - IIS is used to host the Web Pages on the Presentation Tier
D: - Secure Sockets is used on the Presentation tier to create SSL
E: - ASP.NET is used to create the Web Pages on the Presentation Tier
125. (Refer the EXHIBIT given below.)
Case Study
You need to identify the primary keys, foreign keys and attributes for the Loan Request table (See screen shot for question type)
A. Primary Key: Loan Identified
Attribute: Name
Employer
Loan Amount
Address
Foreign Key: Loan Type Identifier
B. Primary Key: Loan Type Identifier
Attribute: Name
Loan Amount
Employer
Credit History Identifier
Address
Foreign Key: Loan Identifier
C. Primary Key: Loan Identifier
Attribute: Name
Address
Employer
Loan Amount
Foreign key: Credit History Identifier
Loan Type Identifier
Answer: A
.

According to Emily, this is the way that it's structured.
Credit history doesn't factor into it. I disagree, but, hey, if I knew everything, I wouldn't be on braindumps.
If I had my own way… I would have all the Loan Applicant details in a separate table (see database diagram below) !!! But since we’re keeping the existing original database database structure… I guess this is how its going to be ?!

126. Woodgrove Bank sets a response time goal of five seconds for customers on dial-up Internet connections. The IT department establishes that dial-up connections average 40 kilobits per second. For a typical Web form, the time between the user’s click and the generation of the server’s response averages 500 milliseconds.
What is the maximum allowable size of the server’s response?
Case Study
A. 11.3 kilobytes
B. 22.5 kilobytes
C. 36.8 kilobytes
D. 90.1 kilobytes
Answer: B
No of Kilobits per second: 40
No of Kilobytes per second: 40 / 8 = 5
Server response overhead: 500 milliseconds or (0.500 seconds)
Maximum no of kilobytes in 4.5 seconds (inclusive of server response overhead) = 5 X 4.5 = 22.5
127. Woodgrove Bank requires a standard appearance for all Web applications. Standards are expected to change periodically. You need to enforce these standards and reduce maintenance time.
What should you do?
Case Study
A. Create a Microsoft Visual Studio .NET Enterprise template.
B. Create a sample HTML page.
C. Create a sample ASP.NET Web form.
D. Create a cascading style sheet.
Answer: D
IT Manager: "Our standard includes colours, fonts, and the position of the company logo.".
• Cascading Style Sheets can set the colour, size, font and behaviour of the HTML elements on a web page.
• Using Cascading Style Sheets also reduces maintenance time as formatting can be maintained in one location, so that you only need to make changes once for an entire application. This is possible if you are using Global/External styles defined in a style sheet file (.CSS), there is no need to make changes to the application here.